Table of Contents
Throttling and Blocking Users
Introduction
- In February 2023 we introduced an enhancement to MESHdesk and APdesk that allows you to throttle or block selected WiFi clients.
- Sometimes the need arise to block a specified user on the WiFi network without disrupting the other users who are also connected. With this enhancement it can be done in a snap.
- With capped LTE products there is a risk of using 'to much' data when using streaming services like YouTube. A few mouse clicks allow you to put a speed limit on WiFi clients in order to quickly and effectively reduce their data consumption.
Blocking Junior's friend
- Nothing like a real life example.
- So Junior's friend came over and they were going to do some gaming.
- Junior's friend is a nice guy but the laptop he came with looks a bit dodgy.
- Soon after he connects to the WiFi the other siblings started with the Daddy the WiFi is broken drill.

- Now we can try our new feature out to block the chap.
- We go to MESHdesk; select our mesh network and click the view icon.
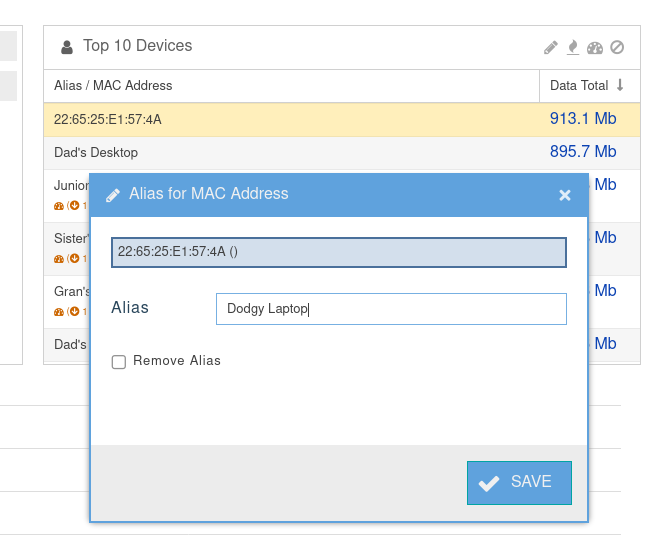
- Note that the top user is a MAC Address we have not yet give a name to. We can safely assume it must be the dodgy laptop.
- Click on the Pencil Icon in the heading bar of Top 10 Devices to pop-up the Alias for MAC Address window.
- After you created the alias for the device; click on Block Device (far right icon) in the heading bar to pop up the Block MAC Address window.
- Since our suspicion about the laptop seems to be valid we will go to the extreme and add a Cloud Wide block.
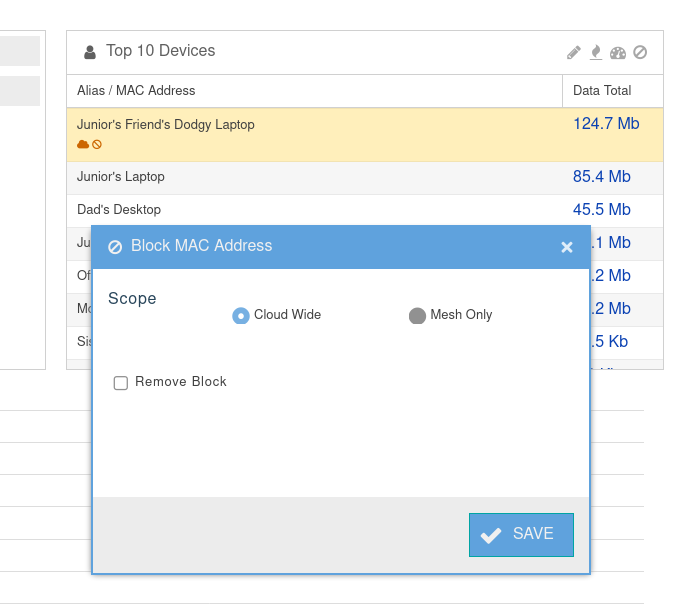
- Note we will have a visual indication of the devices that are throttled or blocked.
Slowing Junior Down

- We got a nice Internet deal from one of our mobile providers with a capped month to month product.
- Unfortunately since the LTE Connection is good some of the streaming sites Junior visits are opportunistic and streams had a high resolution which in turns deplete our data cap even before the month is over.
- Since we are pro-active we select all the kids devices and apply a speed limit to them.
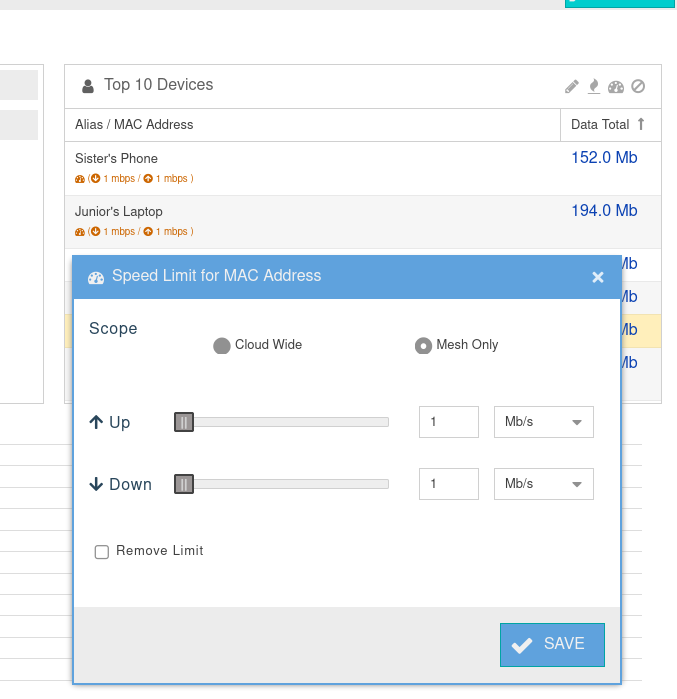
- Again notice that we have a visual indication of the speed limit and also how much it is on those devices that are limited.
Speed test results
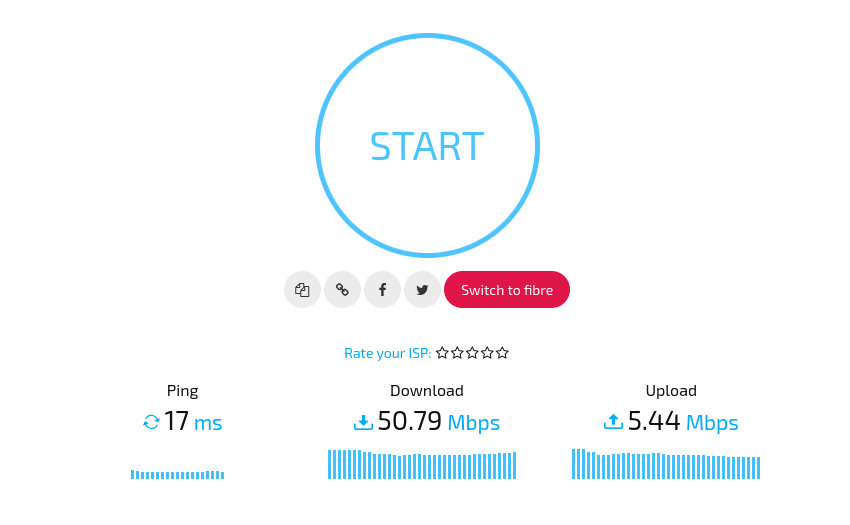
- Speedtest with no speed limit applied
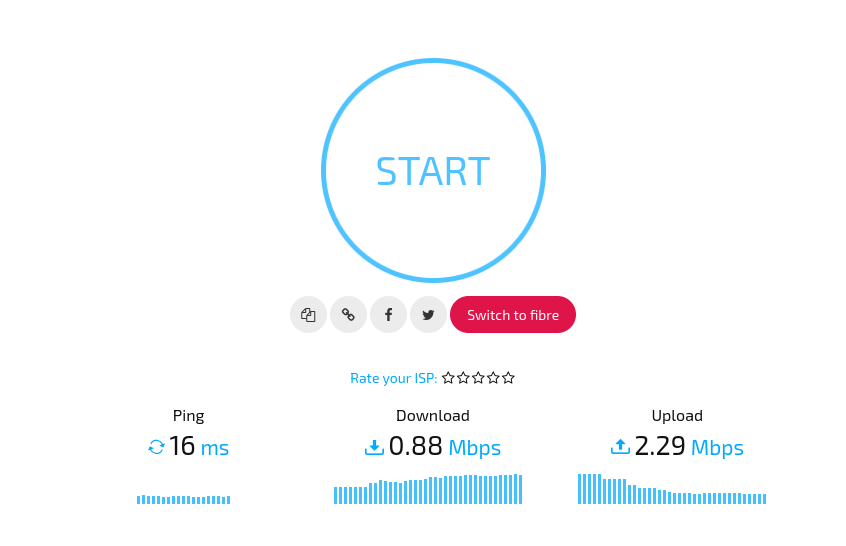
- Speedtest with 1Mbps Upload and 1Mbps Download speed limit applied
Going Back In Time
- You might have noted that up to now we only offered the opportunity for you to select recently connected devices and apply a block or speed limit on them.
- If you blocked someone and a month pass by we still give you an applet with which you can manage these devices.
- Under Meshes and AP Profiles is a Blocked and Speed Limited Devices button.
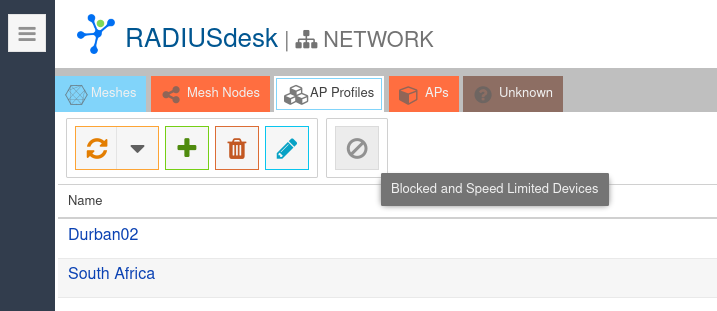
- When you click the button a new closable tab will open.
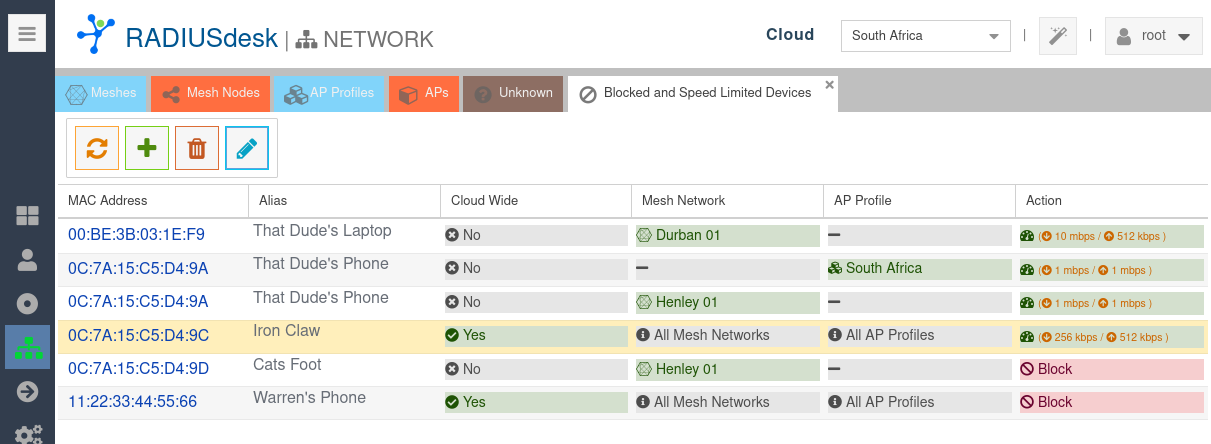
- Here you can see the current entries for the Cloud and Meshes and AP Profiles falling under the selected Cloud.
- This applet allows you to Add, Edit and Delete entries.
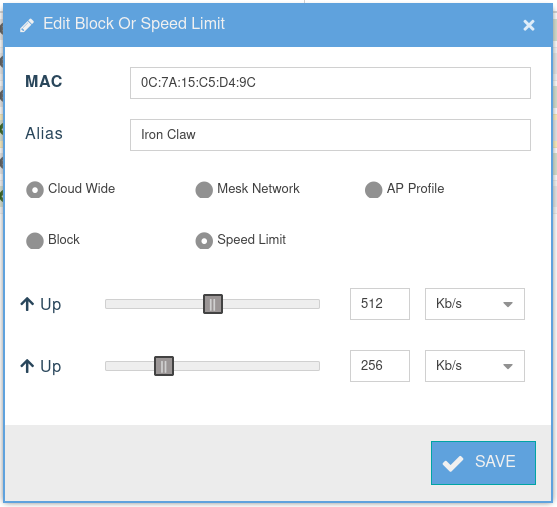
Technical Details
- If you are an old hand with Linux you are probably very familiar with iptables.
- In the old days firewalls were done using iptables and in case you needed to do packet management on layer two you would use ebtables.
- Fast forward to today and we have the much more advanced and user friendly nftables.
- nftables allows you to do packet management on layer three and layer two.
- OpenWrt version 22.03 migrated to use nftables instead of iptables.
- We took the opportunity to take advantage of this improvement with our per device block and speed limit feature.
- This means that the feature will require OpenWrt version 22.03 or higher based firmware to work correct.
- One aspect which makes our implementation unique is the fact that we work on layer two and not layer three.
- The reason for this is that MESHdesk and APdesk allows you to create bridged networks where the IP Address management (DHCP) can be done by another device on the network.
- By working on layer two it allows us to block and apply speed limits without the requirement to know the IP Address of a device.
- You will need the compulsory kmod-nft-bridge nftable module . Make sure it is included with the OpenWrt based firmware.
- Every time you apply or remove a block or speed limit the affected Access Points will be instructed to fetch their latest firewall settings from the controller.
- The utility script that does this is /etc/MESHdesk/utils/fetch_firewall.lua.
- If MQTT (Real time) support is enabled this will happen in real time else it should happen on the next heartbeat that the Access Point sends through which is typically in less than one minute.
- The meshdesk bridge table is where things are happening.
- You can inspect the table using the following command nft -e -a list table bridge meshdesk.
- During startup the Access Point will also, as part of the configuration data sent to it, have a firewall section included (if there is devices that needs to be blocked or speed limited).
- This will then be applied as part of the setup routine.