This is an old revision of the document!
LDAP and Role Based Access (RBA)
- RADIUSdesk allows the admin of a cloud to be in one of three possible roles.
- Admin
- Operator
- View
- The rights of the admin is dictated by the role they are in.
- This document will cover the optional configuration that allows you to map LDAP groups to the respective available roles.
Group Attribute
- The RADIUSdesk implementation allows you to specify the LDAP attribute which contains the groups a user belongs to.
- If you have an OpenLDAP deployment, you might have to add the memberof overlay.
- This link describes the process in more detail: https://tylersguides.com/guides/openldap-memberof-overlay/
- If you have an Active Directory deployment, make sure the user that does the initial bind can read the memberOf attribute.
- This link covers the items you need to double check: http://www.michaelm.info/blog/?p=1435
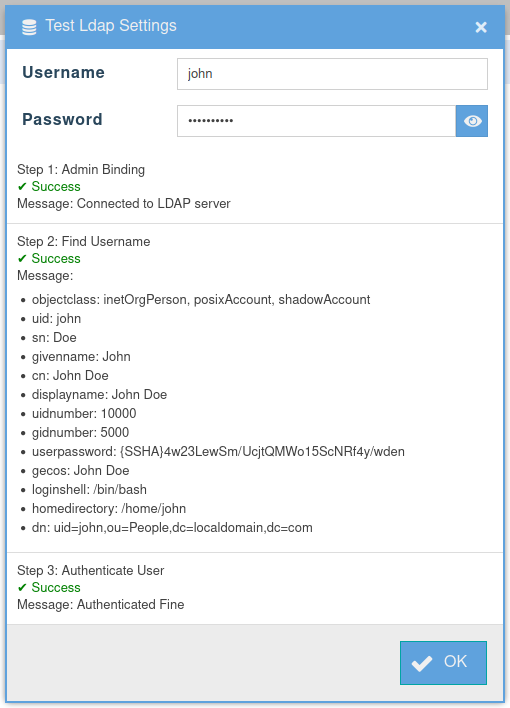
LDAP Authentication Process
Bind (Initial Connection)
- Client connects: The LDAP client (e.g., a user authentication script) connects to the LDAP server.
- Bind request: The client sends a bind request to the server, which includes the username (or DN) and password.
- Server authenticates: The server checks the username and password against its stored credentials.
- Bind response: If the credentials are valid, the server responds with a bind response, indicating a successful connection.
Search
- Search request: The client sends a search request to the server, specifying the search base, scope, filter, and attributes to retrieve.
- Server searches: The server searches its directory based on the client's request.
- Search response: The server responds with a search response, containing the matching entries and their attributes.
Bind on Search Result with Password
- Client selects entry: The client selects an entry from the search results.
- Client extracts DN: The client extracts the DN (distinguished name) from the selected entry.
- Bind request with DN and password: The client sends a new bind request to the server, using the extracted DN and the user-provided password.
- Server authenticates: The server checks the DN and password against its stored credentials.
- Bind response: If the credentials are valid, the server responds with a bind response, indicating a successful authentication.
Configure LDAP
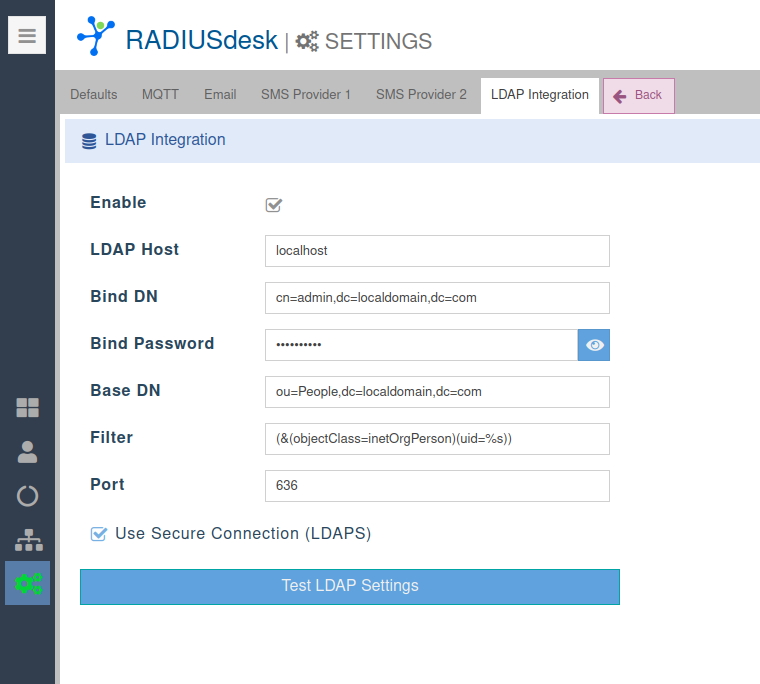
- LDAP Integration is configured under the settings tab.
- One item that needs a bit more explanation is Filter.
- The filter contains a special character (%s) which will be substituted with the username that the user provide to log in.
- For active directory it will typically be (&(objectClass=user)(samaccountname=%s)).
- This filter will be applied when searching to find the DN of the user who needs to be authenticated.