Introduction
- RADIUSdesk has become a popular choice for enterprise deployments due to its flexibility and a user-friendly and versatile interface.
- We now also offer our enterprise customers the option of LDAP integration for managing administrators within the RADIUSdesk system.
- In this document, we will cover the configuration and testing of LDAP integration in RADIUSdesk.
Required Packages
- We use the Authentication Plugin available with CakePHP v4 and CakePHP v5 as the foundation for the LDAP integration.
- In the past we used the Auth Component which is now being replaced by the Authentication and Authorization Plugins in more recent versions of CakePHP.
- The rdcore git code from 15 February onward will have the Authentication plugin included and active.
- To add LDAP capability you also need to install the LDAP php library on the system hosting RADIUSdesk.
sudo apt-get install php-ldap
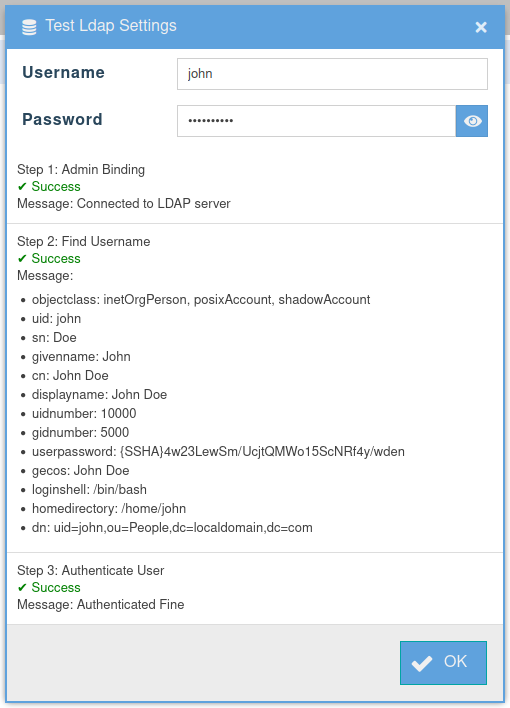
LDAP Authentication Process
Bind (Initial Connection)
- Client connects: The LDAP client (e.g., a user authentication script) connects to the LDAP server.
- Bind request: The client sends a bind request to the server, which includes the username (or DN) and password.
- Server authenticates: The server checks the username and password against its stored credentials.
- Bind response: If the credentials are valid, the server responds with a bind response, indicating a successful connection.
Search
- Search request: The client sends a search request to the server, specifying the search base, scope, filter, and attributes to retrieve.
- Server searches: The server searches its directory based on the client's request.
- Search response: The server responds with a search response, containing the matching entries and their attributes.
Bind on Search Result with Password
- Client selects entry: The client selects an entry from the search results.
- Client extracts DN: The client extracts the DN (distinguished name) from the selected entry.
- Bind request with DN and password: The client sends a new bind request to the server, using the extracted DN and the user-provided password.
- Server authenticates: The server checks the DN and password against its stored credentials.
- Bind response: If the credentials are valid, the server responds with a bind response, indicating a successful authentication.
Configure LDAP
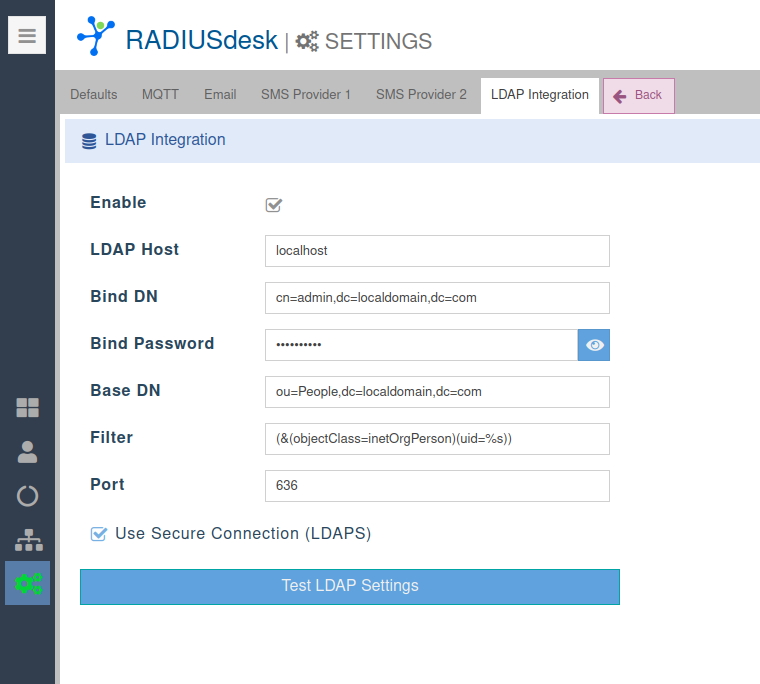
- LDAP Integration is configured under the settings tab.
- One item that needs a bit more explanation is Filter.
- The filter contains a special character (%s) which will be substituted with the username that the user provide to log in.
- For active directory it will typically be (&(objectClass=user)(samaccountname=%s)).
- This filter will be applied when searching to find the DN of the user who needs to be authenticated.